portfolio communications
Cybersecurity
solutions
Cybersecurity
Cybersecurity isn’t just IT’s problem anymore, it’s a boardroom priority.
Learn how Cyber Risk Quantification (CRQ) translates technical threats into business-aligned decisions, giving executives clarity, accountability, and a financial view of risk.
When it comes to cybersecurity, many leaders are in over their heads. It’s an increasingly complex threat landscape and hiring/retention challenges continue to soar.
Technology advisors have a massive role to play in cybersecurity. Simply put, customers are overwhelmed keeping up with all of the latest technological advancements and AI-driven threats. Now more than ever, business leaders are depending on advisors to know how they should be leveraging new tools and which deliver the most value.
Protect your systems and reduce technical vulnerabilities with complete and scalable risk and compliance frameworks and proper employee training
Leverage Portfolio’s security experts with certifications including CISSP, CISM, CRSC, CCSK, COBIT, and GSEC GOLD to help with anything from Impact Assessments to Cyber Security Insurance audits to optimize posture before policy renewal negotiations.
Companies can now use AI to help with many different tasks, including:
- Threat detection and response: AI analyzes vast amounts of security data (logs, network traffic, endpoint activity) to identify patterns and anomalies that indicate malicious behavior.
- Endpoint patching and remediation: Large organizations often have hundreds of thousands of endpoints to manage. AI helps identify vulnerable endpoints, prioritize risks, and automate patching efforts.
- Phishing and email security: Threat actors are increasingly targeting end-users with AI-driven phishing scams. Natural language processing (NLP) and machine learning algorithms can analyze email content, sender behavior, and attachments to detect harmful activity and alert users about incoming threats.
- User and entity behavior analytics (UEBA): By continuously monitoring user activity, UEBA helps detect compromised accounts and insider threats. AI enhances this process by connecting the dots between disparate events, providing greater visibility into potential risks.
- Automated incident response: Companies are increasingly integrating AI into security orchestration, automation, and response (SOAR) platforms to automate different stages of the response process.
SentinelOne, CrowdStrike, and Cisco just unveiled at RSA 2025…summarizing how they will leverage Agentic AI within their solutions.
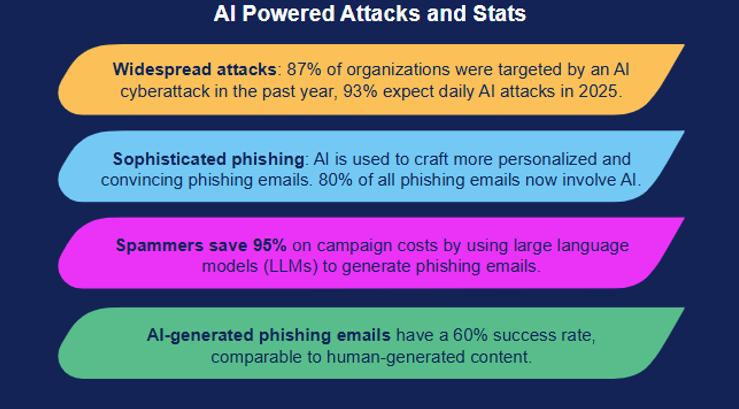
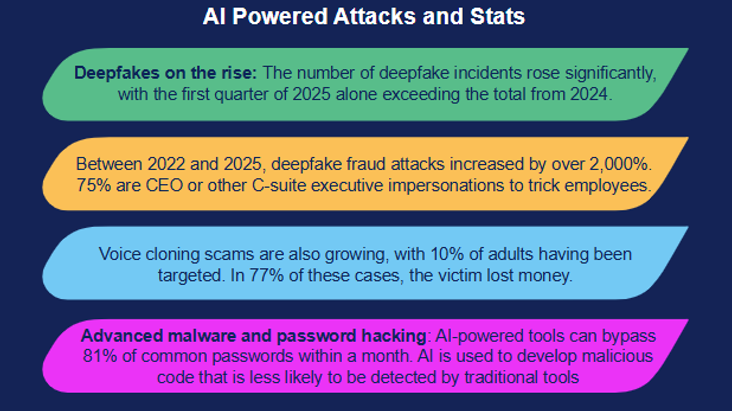

Portfolio can take you through a quick, no commitment, innovative security assessment (short or long versions) to help you perform due diligence and help prevent a breach.

